Professional Credentials
Discover my verified certifications and qualifications in cybersecurity
Accreditation and Achievements
The Google Cybersecurity Certificate
Overview
Earning the Google Cybersecurity Certificate involved completing eight comprehensive courses developed by Google. These courses include hands-on, practice-based assessments designed to prepare participants for entry-level roles in cybersecurity.
This certification has equipped me with the foundational knowledge and practical skills necessary to embark on a successful career in cybersecurity.
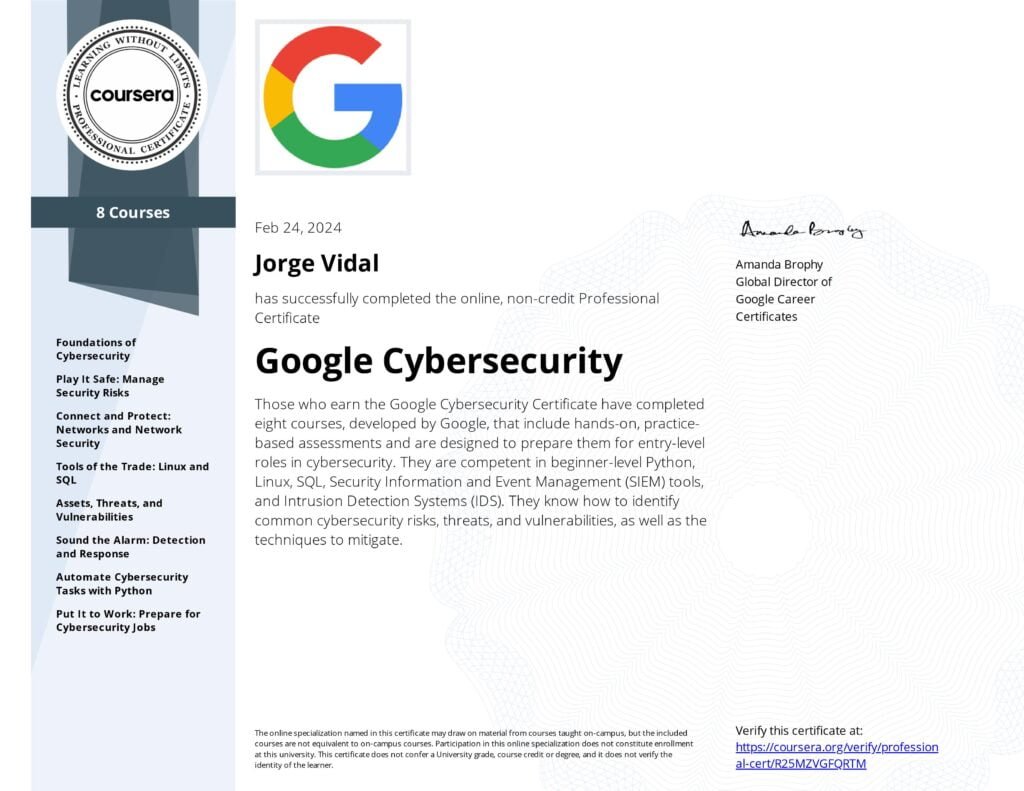
Skills Gained
- Python Programming: Proficiency in beginner-level Python for automating cybersecurity tasks.
- Linux: Competency in using Linux for managing and securing systems.
- SQL: Knowledge of SQL for database management and security.
- Security Information and Event Management (SIEM) Tools: Ability to utilize SIEM tools for monitoring and analyzing security events.
- Intrusion Detection Systems (IDS): Skills in setting up and managing IDS to detect and respond to threats.
- Cybersecurity Risk Management: Understanding of how to identify and mitigate common cybersecurity risks, threats, and vulnerabilities.
Courses Completed
- Foundations of Cybersecurity: Introduction to core cybersecurity concepts.
- Play It Safe: Manage Security Risks: Techniques for managing and mitigating security risks.
- Connect and Protect: Networks and Network Security: Fundamentals of network security.
- Tools of the Trade: Linux and SQL: Hands-on experience with Linux and SQL for cybersecurity purposes.
- Assets, Threats, and Vulnerabilities: Identifying and addressing various cybersecurity threats and vulnerabilities.
- Sound the Alarm: Detection and Response: Detection and response strategies for cybersecurity incidents.
- Automate Cybersecurity Tasks with Python: Using Python to automate cybersecurity tasks.
- Put It to Work: Prepare for Cybersecurity Jobs: Preparation for real-world cybersecurity roles.
Bachelor of Business Administration in Cybersecurity
Overview:
I earned my Bachelor of Business Administration in Cybersecurity from the University of Texas at San Antonio (UTSA). This program provided a comprehensive education in cybersecurity, blending business principles with technical skills to prepare me for a professional career in the field.
This degree has equipped me with a robust foundation in both business and technical aspects of cybersecurity, preparing me to tackle complex challenges in the field and contribute effectively to any cybersecurity team.

Key Courses and Learning Outcomes
IS 1003. Unlocking Cyber
- Overview: Covered core security concepts and discussed common challenges and threats faced by individuals, organizations, and nations through current events, case studies, and career profiles.
- Skills Learned: Problem-solving techniques, analytical skills, report writing, and hands-on experience with virtualization, Linux, and Command Line tools.
IS 3423. Network Security
- Overview: Provided a foundation in networking technologies essential for creating secure networks.
- Skills Learned: Basic cryptography, secure networking protocols, logical and physical security management, and understanding of security devices.
IS 3033. Operating Systems and Security
- Overview: Emphasized real-world security and performance challenges of operating systems.
- Skills Learned: Process scheduling, memory management, I/O devices, file systems, OS hardening, secure server configuration, system-level firewalls, kernel security modules, logging, and anti-malware measures.
IS 4483. Digital Forensic Analysis I
- Overview: Introduced fundamental data structures, software tools, and forensic analysis techniques used in digital forensic investigations.
- Skills Learned: File system forensic analysis, evidence collection, examination, evaluation, and reporting to establish intent, culpability, motive, means, methods, and loss resulting from cybercrimes.
IS 4543. Cyber Attack and Defend I
- Overview: Bridged the gap between secure network implementation and actual cyber threats.
- Skills Learned: Red team assessments, security policy creation, understanding hacker techniques, and monitoring attack impacts.
IS 3413. Telecommunications and Networking
- Overview: Presented principles of data transmission in telecommunications and networks.
- Skills Learned: Network hardware and topologies, the OSI model, TCP/IP stack, routing protocols, IP addressing and subnetting, Ethernet, wireless, radio, mobile, SDWAN, VoIP, IoT, and cloud/edge communications and protocols.
Achievements
- GPA: 3.5
- Hands-on Labs: Engaged in practical labs using industry-standard tools and techniques.
- Project Work: Completed various projects that reinforced theoretical knowledge with practical application.
- Recognition: Received commendations from faculty for exceptional performance in cybersecurity-related coursework and projects.
